A lightning talk at
NANOG 48, Austin, Texas, 22 Feb 2010,
by
John Kristoff,
Team Cymru.
See
RFC 5575.
Update: PDF of presentation slides here.
+--------+--------------------+--------------------------+
| type | extended community | encoding |
+--------+--------------------+--------------------------+
| 0x8006 | traffic-rate | 2-byte as#, 4-byte float |
| 0x8007 | traffic-action | bitmask |
| 0x8008 | redirect | 6-byte Route Target |
| 0x8009 | traffic-marking | DSCP value |
+--------+--------------------+--------------------------+
A few selected points:
-
Dissemination of Flow Specification Rules
-
Think of filters(ACLs) distributed via BGP
-
BGP possibly not the right mechanism
-
Multi-hop real-time black hole on steroids
-
Abuse Handler + Peering Coordinator
= Abeering Coordinator?
-
Traditional bogon feed as source prefix flow routes
-
A la carte feeds (troublesome IP multicast groups, etc.)
-
AS path prepend++
-
Feed-specific community + no-export
He showed some examples of specs for flows
(I can’t type fast enough to transcribe those).
Trust issues for routes defined by victim networks.
Research prototype is set up. For questions, comments, setup, contact:
http://www.cymru.com/jtk/
I like it as an example of collective action against the bad guys.
How to deal with the trust issues seems the biggest item to me.
Hm, at least to the participating community, this is a reputation system.
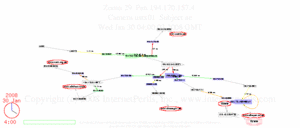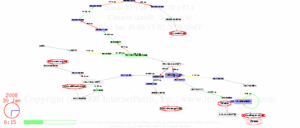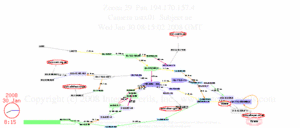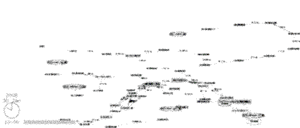
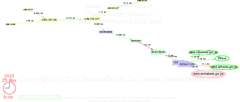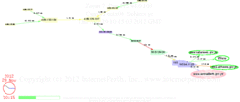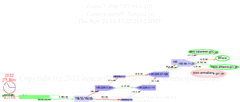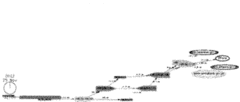 as shown in the animation here and
detailed in the PerilWatch from InternetPerils.
That timing closely matched the
10:26 AM GMT Syrian disconnect time reported by Renesys.
This is very reminiscent of
Mubarak disconnecting Egypt 22:30 GMT 20 January 2011.
This tactic didn’t help Mubarak’s regime in Egypt, and it probably won’t
help Assad’s regime in Syria; rather the opposite: people don’t like
their Internet being turned off.
And it tends to cause the international community to rally around the rebels.
as shown in the animation here and
detailed in the PerilWatch from InternetPerils.
That timing closely matched the
10:26 AM GMT Syrian disconnect time reported by Renesys.
This is very reminiscent of
Mubarak disconnecting Egypt 22:30 GMT 20 January 2011.
This tactic didn’t help Mubarak’s regime in Egypt, and it probably won’t
help Assad’s regime in Syria; rather the opposite: people don’t like
their Internet being turned off.
And it tends to cause the international community to rally around the rebels.

 On 27 January 2011 the Egyptian government cut off cell phone and
Internet access to the outside world.
Here’s what routing looked like to six destinations inside Egypt
as that happened.
The InternetPerils
On 27 January 2011 the Egyptian government cut off cell phone and
Internet access to the outside world.
Here’s what routing looked like to six destinations inside Egypt
as that happened.
The InternetPerils