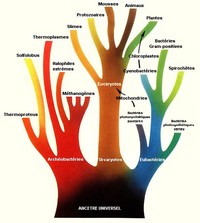
Why are there so many wildfires in the U.S. west?
Cheatgrass grows where land has been disturbed by overgrazing:
Why are there so many wildfires in the U.S. west?
Cheatgrass grows where land has been disturbed by overgrazing:
So basically 20,000 public lands welfare ranchers have a death grip on science policies applied to western public lands.Hey, it could be worse!— comment by kt, July 17th, 2007 at 8:13 am commmenting on Why cheatgrass wins, by Ralph Maughan, Ralph Maughan’s Wildlife News, July 16th, 2007
Today was the hottest day in Serbia ever since the temperature has been measured, 45 C [113 F].This is what you get when you sell off the public good and the equipment to protect it to private interests: your country burning down.If we we Serbs were truly interested in our survival as a nation, we’d be scrambling to get some modern hardware for dealing with ecological catastrophes. It’s been ten years since Milosevic sold off our forest fire-fighting aircraft and pocketed the money.
— Serbia and the Flames, Jasmina Tešanović, BoingBoing, Tuesday, July 24, 2007
-jsq