 McAfee PR of today,
McAfee Quarterly Threat Report Sees Social Media Worm Resurgence as Spam Rises Dramatically:
Targeted Attacks Continue Rise; “Pump and Dump” Returns
with Record Stock Market Highs
McAfee PR of today,
McAfee Quarterly Threat Report Sees Social Media Worm Resurgence as Spam Rises Dramatically:
Targeted Attacks Continue Rise; “Pump and Dump” Returns
with Record Stock Market Highs
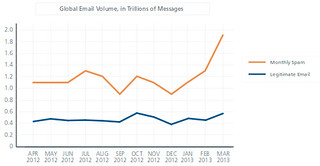
McAfee Labs today released the McAfee Threats Report: First Quarter 2013, which reported a significant spike in instances of the Koobface social networking worm and a dramatic increase in spam. McAfee Labs also saw continued increases in the number and complexity of targeted threats, including information-gathering Trojans and threats targeting systems’ master boot records (MBRs).
McAfee Labs found almost three times as many samples of Koobface as were seen in Continue reading