FBI indicts, and in some cases gets guilty pleas or sentences,
eight people they say were involved in botnet-related activities:
FBI indicts, and in some cases gets guilty pleas or sentences,
eight people they say were involved in botnet-related activities:
Secure Computing’s prinicipal research scientist Dmitri Alperovitch was quite happy about the news.Indeed, good news.“We welcome this news and applaud the FBI’s efforts and law enforcement worldwide in attempting to cleanup the cesspool of malware and criminality that the botmasters have promoted,” Alperovitch said in a press release. “Since botnets are at the root of nearly all cybercrime activities that we see on the Internet today, the significant deterrence value that arrests and prosecutions such as these provide cannot be underestimated.”
— FBI Cracks Down (Again) on Zombie Computer Armies, By Ryan Singel, Threat Level, November 29, 2007 | 4:54:32 PM
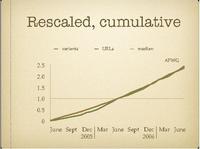
Now where are the metrics to show how much effect this actually had on number of botnets, number of bots, criminal activities mounted from bots, etc.? Baseline, ongoing changes, dashboard, drilldown?
-jsq
PS: Interestingly, every blog or press writeup I’ve seen about this misuses the word “hacker” to apply to these crackers, yet the actual FBI announcement never makes that mistake: it says cyber crime.