Reviewing Bruce Schneier’s 2004 book Secrets and Lies,
much of which was written in 2000, reminds us of something really basic.
You can’t just fix security.
Security is a process, most of which is about knowing what’s going on.
Detection is more important than prevention.
To which I add that for detection we need comparable Internet-wide metrics
on security performance so every organization can see
what’s going on and will have incentive to do something about it
because its customers and competitors can see, too.
Sound familiar?
That’s what
SpamRankings.net is about.
Joe Zack posted in Joezack.com on Bastille Day, 14 July 2013,
Secrets and Lies: Nine Years Later,
2. “Detection is much more important than prevention”
Schneier keeps coming back to this point. He had this epiphany in
1999 that “it is fundamentally impossible to prevent
attacks” and “preventative countermeasures fail all the
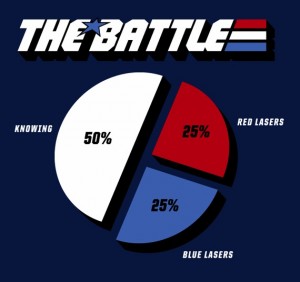 time.” Security is “about risk management, that the
process of security was paramount, that detection and response was
the real way to improve security.” (emphasis mine)
time.” Security is “about risk management, that the
process of security was paramount, that detection and response was
the real way to improve security.” (emphasis mine)
I had formerly thought of security as largely being about
prevention. A year ago, if you have asked me about
“InfoSec” I might have prattled on about firewalls,
injection attacks, encryption and good passwords. That’s still
important, but now I know that there’s a lot more to it.
Zack says he thinks Schneier was like Nostradamus for having such
insight before
NSA PRISM and even before Facebook.
Sure, Bruce has always been ahead of his time.
But that basic insight was not unique to him, and Continue reading →



 On 27 January 2011 the Egyptian government cut off cell phone and
Internet access to the outside world.
Here’s what routing looked like to six destinations inside Egypt
as that happened.
The InternetPerils
On 27 January 2011 the Egyptian government cut off cell phone and
Internet access to the outside world.
Here’s what routing looked like to six destinations inside Egypt
as that happened.
The InternetPerils


