In addition to snowshoe spam taking 7 of the top 10  U.S. SpamRankings.net for May 2012, one of the snowshoe spamming companies, CDM, outspammed every other organization in the world! CDM’s AS 6428 outspammed even chronic world winner
U.S. SpamRankings.net for May 2012, one of the snowshoe spamming companies, CDM, outspammed every other organization in the world! CDM’s AS 6428 outspammed even chronic world winner  Vietnam PT.
Vietnam PT.
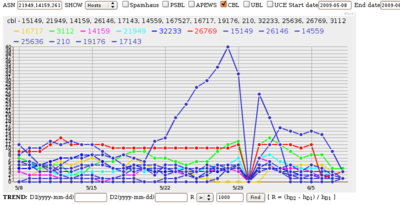
In this graph, you can see CDM leap up from zero in March to 15.7 million spam messages in April and 48.8 million in May, and of course that’s just the messages caught by a few spamtraps.
The same spamtraps never saw more than 56 hosts sending all those messages. That was on 11 May 2012, when they saw 1,989,762 spam messages, for a ratio of 35,531 spam messages per sending host. That’s not exactly the old botnet low-and-slow technique. Snowshoe spam: it’s already in prime time!
And remember, CDM is not a hosting center: it’s an ISP. CDM continues to illustrate that snowshoe spam is no longer confined to the traditional profile of infesting hosting centers.
-jsq