
Shing Yin Khor of Fox Interactive Media, which owns MySpace, gave an entertaining talk at APWG in which she gave a good case that MySpace has mostly eliminated phishing ads on MySpace and is busily suppressing other phishing.
Throwing money at the issue of phishing actually works.
MySpace’s anti-phishing forces include former law enforcement people, including a former federal and state prosecutor, a former L.A. D.A., and a former FBI agent. They have successfully sued spam king Scott “ringtones” Richter and his CPA empire.
MySpace does have an advantage in actually hosting all displays and messages.
It’s good to be a many-hundred-million shopping mall. She didn’t say that; I did. She did say they use MySpace specific measures such as education via Tom’s profile. Tom was one of the founders of MySpace. Every new user gets Tom as a friend, so his online persona (pictured) has 240 million friends, so that’s a channel that reaches most of their users. She did say:
Education is just as important as technical measures.
What works on MySpace will work on other social network sites.
But Shing’s theme of pro-active measures against phishing and spam is one other organizations could take to heart. Don’t think you can do nothing: you can.
Of course, if you have fewer than 200 million users, you may want to band together with other organizations, for example by joining APWG. Even MySpace does.
 McAfee PR of today,
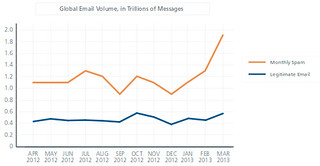
McAfee Quarterly Threat Report Sees Social Media Worm Resurgence as Spam Rises Dramatically:
Targeted Attacks Continue Rise; “Pump and Dump” Returns
with Record Stock Market Highs
McAfee PR of today,
McAfee Quarterly Threat Report Sees Social Media Worm Resurgence as Spam Rises Dramatically:
Targeted Attacks Continue Rise; “Pump and Dump” Returns
with Record Stock Market Highs




 Shing Yin Khor of Fox Interactive Media, which owns MySpace, gave an entertaining talk at APWG in which she gave a good case that MySpace has mostly eliminated phishing ads on MySpace and is busily suppressing other phishing.
Shing Yin Khor of Fox Interactive Media, which owns MySpace, gave an entertaining talk at APWG in which she gave a good case that MySpace has mostly eliminated phishing ads on MySpace and is busily suppressing other phishing.



