Category Archives: Security
Quis custodiet ipsos medici?
 Internet security is in a position similar to that of safety in the medical industry. Many doctors have an opinion like this one,
quoted by
Kent Bottles:
Internet security is in a position similar to that of safety in the medical industry. Many doctors have an opinion like this one,
quoted by
Kent Bottles:
“Only 33% of my patients with diabetes have glycated hemoglobin levels that are at goal. Only 44% have cholesterol levels at goal. A measly 26% have blood pressure at goal. All my grades are well below my institution’s targets.” And she says, “I don’t even bother checking the results anymore. I just quietly push the reports under my pile of unread journals, phone messages, insurance forms, and prior authorizations.”
Meanwhile, according to the CDC, 99,000 people die in the U.S. per year because of health-care associated infections. That is equivalent of an airliner crash every day. It’s three times the rate of deaths by automobile accidents.
 The basic medical error problems
observed by Dennis Quaid when his twin babies almost died
due to repeated massive medically-administered overdoses
and due to software problems such as
ably analysed by Nancy Leveson
for the infamous 1980s Therac-25 cancer-radiation device
are not in any way unique to computing in medicine.
The solutions to those problems are analogous to some of the solutions
IT security needs: measurements plus
six or seven layers of aggregation, analysis, and distribution.
The basic medical error problems
observed by Dennis Quaid when his twin babies almost died
due to repeated massive medically-administered overdoses
and due to software problems such as
ably analysed by Nancy Leveson
for the infamous 1980s Therac-25 cancer-radiation device
are not in any way unique to computing in medicine.
The solutions to those problems are analogous to some of the solutions
IT security needs: measurements plus
six or seven layers of aggregation, analysis, and distribution.
As Gardiner Harris reported in the New York Times, August 20, 2010, another problem is that intravenous and feeding tubes are not distinguished by shape or color: Continue reading
What we can learn from the Therac-25
 What does
Nancy Leveson’s
classic
analysis of the
Therac-25 recommend?
(“An Investigation of the Therac-25 Accidents,”
by Nancy Leveson, University of Washington and
Clark S. Turner, University of California, Irvine,
IEEE Computer, Vol. 26, No. 7, July 1993, pp. 18-41.)
What does
Nancy Leveson’s
classic
analysis of the
Therac-25 recommend?
(“An Investigation of the Therac-25 Accidents,”
by Nancy Leveson, University of Washington and
Clark S. Turner, University of California, Irvine,
IEEE Computer, Vol. 26, No. 7, July 1993, pp. 18-41.)
“Inadequate Investigation or Followup on Accident Reports. Every company building safety-critical systems should have audit trails and analysis procedures that are applied whenever any hint of a problem is found that might lead to an accident.” p. 47The lesson being that you have to have built-in audit, reporting, transparency, and user visibility for reputation.“Government Oversight and Standards. Once the FDA got involved in the Therac-25, their response was impressive, especially considering how little experience they had with similar problems in computer-controlled medical devices. Since the Therac-25 events, the FDA has moved to improve the reporting system and to augment their procedures and guidelines to include software. The input and pressure from the user group was also important in getting the machine fixed and provides an important lesson to users in other industries.” pp. 48-49
Which is exactly what Dennis Quaid is asking for.
Remember, most of those 99,000 deaths a year from medical errors aren’t due to control of complicated therapy equipment: Continue reading
What about the Therac-25?
Why should anyone assume Dennis Quaid doesn’t know that quality assurance and operational analysis are needed for anything designed or controled by software? The man is a jet pilot, and thus must be aware of such efforts by aircraft manufacturers, airlines, and the FAA. As Quaid points out, we don’t have a major airline crash every day, and we do have the equivalent in deaths from medical errors. Many of which could be fixed by Computerized Physician Order Entry (CPOE).
Or ask the Mayo Clinic: Continue reading
Trust the Doctor, or Trust the Doctor’s Report Card?
“Dr. Kim A. Adcock, the radiology chief at Kaiser Permanente Colorado, created a system that misses one-third fewer cancers on mammograms and “has achieved what experts say is nearly as high a level of accuracy as mammography can offer.” At the heart of the program was his willingness to keep score and confront his doctors with their results. He had to fire three radiologists who missed too many cancers, and he had to reassign 8 doctors who were not reading enough films to stay sharp.”We could use more report cards for physicians, including firing ones with failing grades, and maybe even paying the really good ones more, or at least getting them to teach the others.
-jsq
Dennis Quaid: Medical negligence deaths as many as a major airline crash every day
 People think Internet security is bad (it is),
but let’s look at
medical security:
People think Internet security is bad (it is),
but let’s look at
medical security:
“Actor Dennis Quaid has become an advocate for electronic medical records. In 2007 his 12 day old twins received a massive accidental overdose (10,000 units of heparin instead of 10 units), a near-fatal error that could have been prevented by the kind of bar code technology that the VA has been using for decades. (Yes, folks, sorry, a government institution was decades ahead of privatized healthcare on this.)”I point out that that’s three times the annual deaths from automobiles, and around #5 in leading causes of death in the U.S.“Quaid points out that the widely quote 100,000 accidental deaths every year from medical errors equates to a major airline crash every day.”
-jsq
3FN + FTC = Some Less Spam From Some ASNs
On Tuesday 2 June 2009, the U.S. Federal Trade Commission (FTC) took legal steps that shut down the web hosting provider Triple Fiber network (3FN.net).
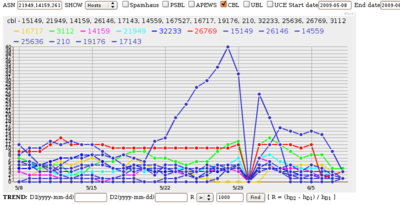
Looking at Autonomous Systems (ASNs) listed in the spam blocklist CBL, Continue reading
VZ Port 587: Good Try
 Back in February, Verizon announced it would start requiring outbound mail go through port 587 instead of port 25 during the next few months. It seemed like a good idea to squelch spam. Most other major ISPs did it. People applauded Verizon for doing it.
Back in February, Verizon announced it would start requiring outbound mail go through port 587 instead of port 25 during the next few months. It seemed like a good idea to squelch spam. Most other major ISPs did it. People applauded Verizon for doing it.
Unfortunately, it seems that if it had any effect it was short-lived. Looking at anti-spam blocklists on a daily basis, a couple of Verizon Autonomous Systems (ASes), AS-19262 and AS-701, do show dips in blocklist listings on the blocklist PSBL in March. But they don’t last.
Spammers are very adaptable, partly because the botnets they use are adaptable. Good try, Verizon.
This information is from an NSF-funded academic research project at the University of Texas at Austin business school. Thanks to PSBL for the blocklist data.
-jsq
Windows Considered Not Ready for the Desktop
0. Premise: free and open software will stay indefinitely. Full stop. You may argue eternally, but free software is the ultimate disruptive technology, moving up from the low ground, replacing complicated and ill-fitting proprietary alternatives at every turn, such as web-browsers, e-mail clients, video players, office software, etc., which at one point cost money, but now most people find that they can no longer justify spending money to buy an upgrade for more “Clippy the Happy Assistant”. Proprietary software will only be able to stay relevant by searching out ever more niche applications, or by massive expenditure on research in high-end applications for which it will take time for the ideas and algorithms to filter down to the greater community, and thus a brief window of profitability will remain. Software patents are nothing but a destructive force to retard innovation, and with more and more of the technology and legal communities realizing this basic fact, software patents are about to go away forever.I think he’s being a bit optimistic about software patents, but no more so than Windows advocates claiming that open software is a flash in the pan. Then he gets into the undeniable stuff, chief of which is:
1.1 History’s greatest playground for malicious software. With unpatched machines on the internet taking only minutes to become infested with viruses, or become a slave bot for massive illegal spamming operations, Windows is a blight on the Internet’s infrastructure.And it keeps getting better. He says he wrote it just as a game, but it pretty much spells out why I don’t use Windows, plus why Windows is a menace to the Internet.
Doing It Wrong: Antivirus Software on Voting Machines
 Xkcd has a point.
And I like the teacher analogy.
Xkcd has a point.
And I like the teacher analogy.
Continuing to fiddle with models of how electronic voting might work while leaving in place demonstrably broken hardware and software produced by companies that over years have demonstrated they either don't understand the problem or have no intention of fixing it: that's fiddling while Rome burns.
-jsq