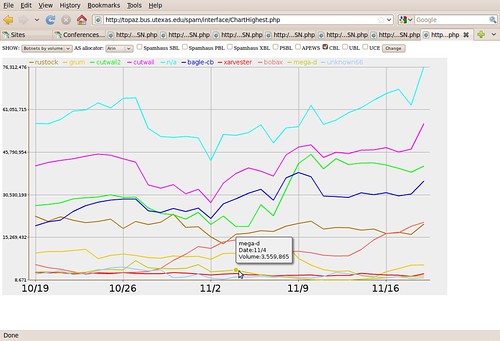
Glitches happen, and this one illustrates how rankings with big differences in spam volume are robust anyway.
A format change in an ancillary data source detected through consistency checks caused recomputations in selected rankings for September, October, and November 2013 in
Classic. (Cloud.
(Cloud. was unaffected).
The old versions are preserved as v1 rankings, and the differences are visible for these overall rankings:
was unaffected).
The old versions are preserved as v1 rankings, and the differences are visible for these overall rankings:
| Geography | Sep 2013 | Oct 2013 | Nov 2013 | |||
|---|---|---|---|---|---|---|
| CBL | PSBL | CBL | PSBL | CBL | PSBL | |
 World World |
CBL** | PSBL | PSBL* | PSBL** | ||
 BE BE |
CBL | PSBL | PSBL | PSBL | ||
 CA CA |
CBL | PSBL | PSBL | PSBL | ||
 TR TR |
CBL | PSBL | CBL | PSBL | PSBL | |
 US US |
CBL* | PSBL | PSBL | PSBL | ||
 Countries Countries |
CBL | PSBL | CBL | PSBL | CBL | PSBL |
| Medical | ||||||
 World World |
CBL** | PSBL | ||||
 US US |
PSBL | |||||
 Countries Countries |
CBL* | PSBL* | ||||
| * Completely unchanged in rank order | ||||||
| ** Unchanged except for dropout final rank | ||||||
So the most noticeable rankings, for World, were Continue reading