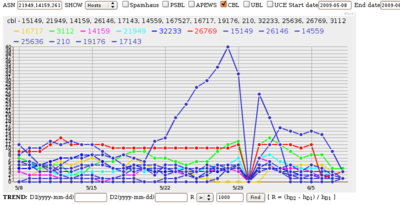
Should Uganda Telecom be counted as a Belgian ISP for outbound spam rankings?
Which matters most: history, topology, business headquarters location, or some other criterion?
These are some questions that come up in designing experiments
in rolling out a reputation system for outbound spam.
More on this in the RIPE Labs article (8 Nov 2010),
Internet Reputation Experiments for Better Security.
 Such experiments can draw on fifty years of social science research
and literature, first crystalized as Social Comparison Theory
by Leon Festinger in 1954,
that indicate that making personal reputation transparent changes personal behavior.
More recent research indicates that the same applies to organizations.
Using anti-spam blocklist data, it is possible to make E-Mail Service Provider
(ESP) behavior (banks, stores, universities, etc., not just ISPs)
in preventing or stopping outbound spam transparent,
and this paper is about experiments to see how the resulting reputation
actually changes ESP behavior.
Such experiments can draw on fifty years of social science research
and literature, first crystalized as Social Comparison Theory
by Leon Festinger in 1954,
that indicate that making personal reputation transparent changes personal behavior.
More recent research indicates that the same applies to organizations.
Using anti-spam blocklist data, it is possible to make E-Mail Service Provider
(ESP) behavior (banks, stores, universities, etc., not just ISPs)
in preventing or stopping outbound spam transparent,
and this paper is about experiments to see how the resulting reputation
actually changes ESP behavior.
-jsq
 Daniel Karrenberg shows an animation related to RIPE Atlas,
RIPE’s new active measurement project using USB-powered dongles scattered around the Internet.
Daniel Karrenberg shows an animation related to RIPE Atlas,
RIPE’s new active measurement project using USB-powered dongles scattered around the Internet.