A surprise in the July
SpamRankings.net rankings:
US medical rankings all went to zero by 14 July.
World medical rankings went from hundreds and thousands to near zero
between 17 and 24 July.
A surprise in the July
SpamRankings.net rankings:
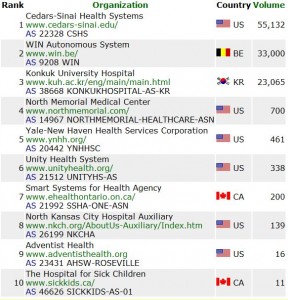
US medical rankings all went to zero by 14 July.
World medical rankings went from hundreds and thousands to near zero
between 17 and 24 July.

That’s in rankings from CBL data. PSBL shows much less data for medical organizations, yet nonetheless the same effect in both world and U.S. medical rankings.
No other rankings showed such a drop.
Did medical organizations actually clean up their act? Or did they just manage to whitelist their netblocks at CBL and PSBL?
Either way, it looks like they noticed SpamRankings.net.
-jsq