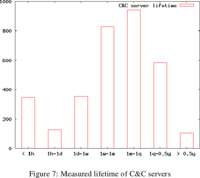
Update: PDF of presentation slides here.
+--------+--------------------+--------------------------+ | type | extended community | encoding | +--------+--------------------+--------------------------+ | 0x8006 | traffic-rate | 2-byte as#, 4-byte float | | 0x8007 | traffic-action | bitmask | | 0x8008 | redirect | 6-byte Route Target | | 0x8009 | traffic-marking | DSCP value | +--------+--------------------+--------------------------+
A few selected points:
- Dissemination of Flow Specification Rules
- Think of filters(ACLs) distributed via BGP
- BGP possibly not the right mechanism
- Multi-hop real-time black hole on steroids
-
Abuse Handler + Peering Coordinator
= Abeering Coordinator? - Traditional bogon feed as source prefix flow routes
- A la carte feeds (troublesome IP multicast groups, etc.)
- AS path prepend++
- Feed-specific community + no-export
Trust issues for routes defined by victim networks.
Research prototype is set up. For questions, comments, setup, contact: http://www.cymru.com/jtk/
I like it as an example of collective action against the bad guys. How to deal with the trust issues seems the biggest item to me.
Hm, at least to the participating community, this is a reputation system.