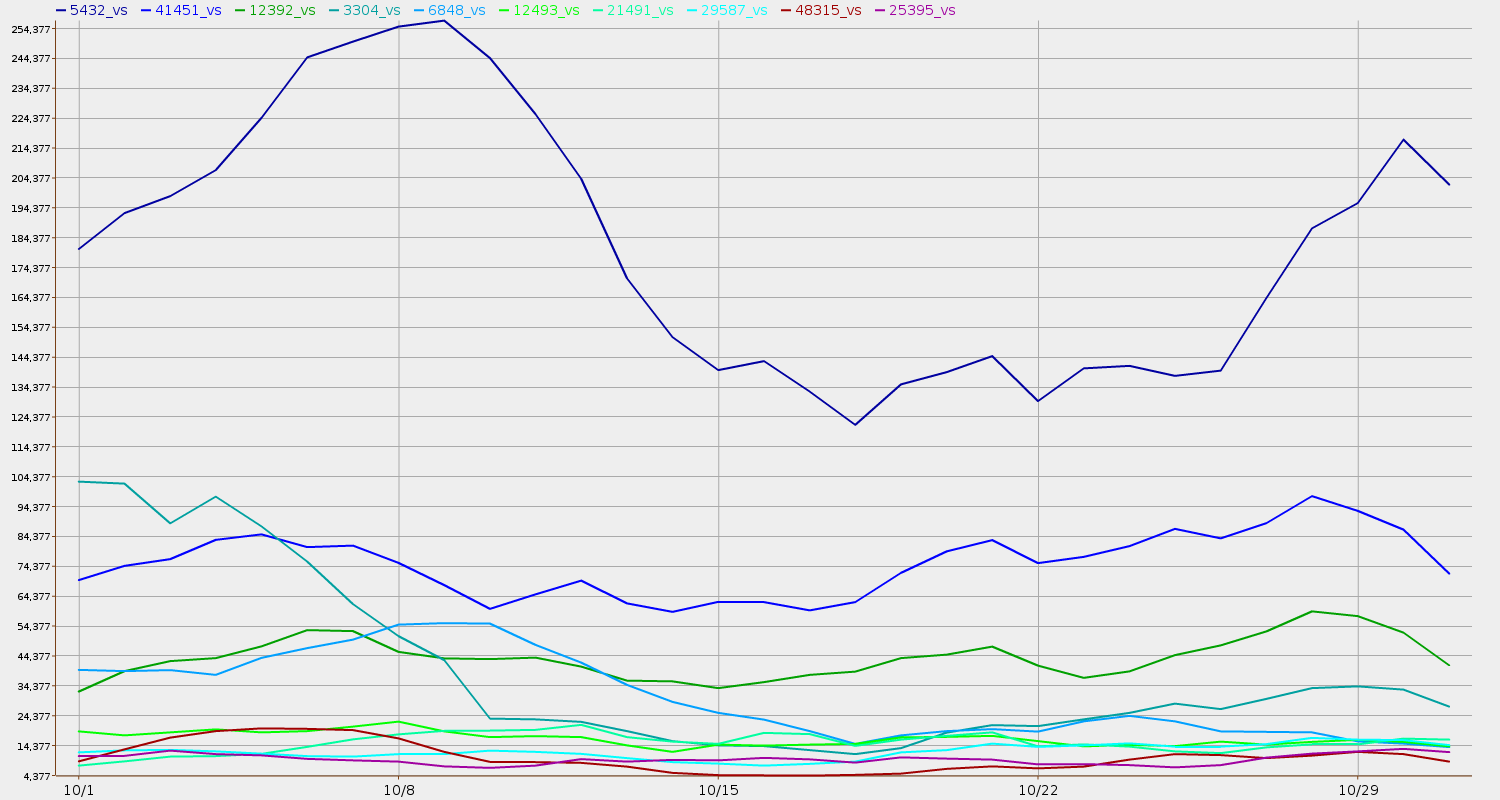
Fahmida Y. Rashid wrote in eWeek.com 8 June 2011, UT Researchers Launch SpamRankings to Flag Hospitals Hijacked by Spammers:
That’s a pretty good explanation for why outbound spam is a proxy for poor infosec.“Poor security measures are generally responsible for employee workstations getting compromised, either by spam or malicious Web content. Once the machine is compromised, the botnet herders can add it to its spam-spewing botnet to send out malware to even more people. The original employee or the organization rarely has any idea the machine has been hijacked for this purpose.”
-jsq


 On 27 January 2011 the Egyptian government cut off cell phone and
Internet access to the outside world.
Here’s what routing looked like to six destinations inside Egypt
as that happened.
The InternetPerils
On 27 January 2011 the Egyptian government cut off cell phone and
Internet access to the outside world.
Here’s what routing looked like to six destinations inside Egypt
as that happened.
The InternetPerils