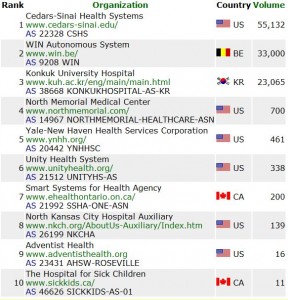
A week ago you may recall most of March’s crop of Ogee spamming ASNs had subsided. Yet there were some contenders coming up from the bottom right corner of the graph.
A week ago you may recall most of March’s crop of Ogee spamming ASNs had subsided. Yet there were some contenders coming up from the bottom right corner of the graph.
Some correspondents say snowshoe spamming such as Ogee is a black swan, unanticipated and short-lived. I say it may be a change in strategy. Others say the actual spam coming out of Ogee is not the same campaigns as we’ve seen from botnets, so spammers are not moving over. To which I say: yet. And if snowshoe spam is big enough to change worldwide SpamRankings.net, and if it continues, that’s a strategy change. We’ll see how all that goes.
Meanwhile, what’s happened in the last week or two?
Top 10 ASNs showing Ogee spam 2012-03-01 to 2012-04-25, SpamRankings.net.
A few of those contenders were just flashes in the pan. But others are still spamming increasingly more.
-jsq




 Cogent’s AS 174.
Cogent’s AS 174. Belarus’ AS 6697 BELPAK-AS
Belarus’ AS 6697 BELPAK-AS