On Tuesday 2 June 2009, the U.S. Federal Trade Commission (FTC) took legal steps that shut down the web hosting provider Triple Fiber network (3FN.net).
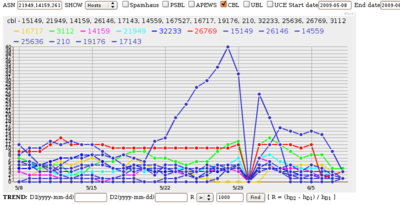
Looking at Autonomous Systems (ASNs) listed in the spam blocklist CBL, Continue reading
On Tuesday 2 June 2009, the U.S. Federal Trade Commission (FTC) took legal steps that shut down the web hosting provider Triple Fiber network (3FN.net).

Looking at Autonomous Systems (ASNs) listed in the spam blocklist CBL, Continue reading
 Gunnar Peterson
asks a question:
Gunnar Peterson
asks a question:
…how do you primarily rely on network security as we have done for the Web’s life, when the Cloud abstracts the network away?Gunnar points out IT security has been using firewalls and SSL as primary security for every network acccess software change since 1995.
In 1999 when SOAP emerged as a firewall-friendly protocol designed for the explicit reason to go through the firewall, that should have been a wake up call to Information Security that the “firewall + SSL” security architecture was past its prime, but here 10 years later we are still hitting the snooze button.Here many years after we lost email for everybody but aging geeks and banks, IT security continues to snooze like Rip van Winkle. While the world changes around it: Continue reading
 Back in February, Verizon announced it would start requiring outbound mail go through port 587 instead of port 25 during the next few months. It seemed like a good idea to squelch spam. Most other major ISPs did it. People applauded Verizon for doing it.
Back in February, Verizon announced it would start requiring outbound mail go through port 587 instead of port 25 during the next few months. It seemed like a good idea to squelch spam. Most other major ISPs did it. People applauded Verizon for doing it.
Unfortunately, it seems that if it had any effect it was short-lived. Looking at anti-spam blocklists on a daily basis, a couple of Verizon Autonomous Systems (ASes), AS-19262 and AS-701, do show dips in blocklist listings on the blocklist PSBL in March. But they don’t last.
Spammers are very adaptable, partly because the botnets they use are adaptable. Good try, Verizon.
This information is from an NSF-funded academic research project at the University of Texas at Austin business school. Thanks to PSBL for the blocklist data.
-jsq
0. Premise: free and open software will stay indefinitely. Full stop. You may argue eternally, but free software is the ultimate disruptive technology, moving up from the low ground, replacing complicated and ill-fitting proprietary alternatives at every turn, such as web-browsers, e-mail clients, video players, office software, etc., which at one point cost money, but now most people find that they can no longer justify spending money to buy an upgrade for more “Clippy the Happy Assistant”. Proprietary software will only be able to stay relevant by searching out ever more niche applications, or by massive expenditure on research in high-end applications for which it will take time for the ideas and algorithms to filter down to the greater community, and thus a brief window of profitability will remain. Software patents are nothing but a destructive force to retard innovation, and with more and more of the technology and legal communities realizing this basic fact, software patents are about to go away forever.I think he’s being a bit optimistic about software patents, but no more so than Windows advocates claiming that open software is a flash in the pan. Then he gets into the undeniable stuff, chief of which is:
1.1 History’s greatest playground for malicious software. With unpatched machines on the internet taking only minutes to become infested with viruses, or become a slave bot for massive illegal spamming operations, Windows is a blight on the Internet’s infrastructure.And it keeps getting better. He says he wrote it just as a game, but it pretty much spells out why I don’t use Windows, plus why Windows is a menace to the Internet.

The eBay-owned company, which runs a Web-based payment system that allows the transfer of funds between bank accounts and credit cards, said browsers that do not have support for blocking identity theft-related Web sites or for EV SSL (Extended Validation Secure Sockets Layer) certificates are considered “unsafe” for financial transactions.Now on the one hand, I think EV SSL is color-coded checklist security candy: Continue reading“In our view, letting users view the PayPal site on one of these browsers is equal to a car manufacturer allowing drivers to buy one of their vehicles without seat belts,” said PayPal Chief Information Security Officer Michael Barrett.
…
Barrett only mentioned old, out-of-support versions of Microsoft’s Internet Explorer among this group of “unsafe browsers,” but it’s clear his warning extends to Apple’s Safari browser, which offers no anti-phishing protection and does not support the use of EV SSL certificates.
— BPayPal Plans to Ban Unsafe Browsers, By Ryan Naraine, EWeek.com, 2008-04-17
 Georgia’s governor wants to standardize information security reporting across
the entire state government:
Georgia’s governor wants to standardize information security reporting across
the entire state government:
The Executive Order calls for a single set of information security reporting standards for all agencies to follow. Currently, state agencies use a variety of reporting standards, making it difficult to measure information security across state government or to track progress from year to year.I think this is a good move. Now how about monthly reporting in a publicly visible web page.Governor Perdue has directed the Georgia Technology Authority (GTA) to work with the Georgia Department of Audits and Accounts and the Governor’s Office of Planning and Budget to develop a reporting format and required content for agency information security reports. Each agency will be responsible for reporting to GTA at the end of the fiscal year. GTA will compile agency reports into a single Enterprise Information Security Report, available by October 31 of each year.
— Gov. Perdue Signs Executive Order Strengthening Georgia’s Information Technology Security, News Report, Government Technology, Mar 20, 2008
-jsq
 Adam Shostack, whose group blog Emergent Chaos
I quote frequently in this blog, has a new book coming out with
co-author Andrew Stewart:
New School of Information Security.
Adam Shostack, whose group blog Emergent Chaos
I quote frequently in this blog, has a new book coming out with
co-author Andrew Stewart:
New School of Information Security.
We think there’s an emerging way of approaching the world, which we call the New School.I haven’t read the book yet, since it’s not published yet, but if it’s like the material he posts in his blog, it’s a good thing.We start with a look at some persistent issues like spam and identity theft. From there, we look at why the information security industry hasn’t just fixed them, and some of the data sources which we rely on and how poor they are. We then look at some new source of data, and new ways of interpreting them, and close with some very practical steps that any individual or organization can take to make things better.
— The New School of Information Security, Adam Shostack, Emergent Chaos, 10 March 2008
One of his commenters doesn’t get it: Continue reading
 Interesting that Germany has more respect for privacy than the U.S. does:
Interesting that Germany has more respect for privacy than the U.S. does:
Government surveillance of personal computers would violate the individual right to privacy, Germany’s highest court found Wednesday, in a ruling that German investigators say will restrict their ability to pursue terrorists.Although apparently Germany also has lazy cops who think spying on individuals is their birthright, just like in the U.S. Not regular police, mind you, butThe Karlsruhe-based Federal Constitutional Court said in a precedent-setting decision that data stored or exchanged on a personal computer is effectively covered under principles of the constitution that enshrine the right to personal privacy.
“Collecting such data directly encroaches on a citizen’s rights, given that fear of being observed … can prevent unselfconscious personal communication,” presiding judge Hans-Juergen Papier said in his ruling.
— Court Shoots Down Computer Surveillance, By MELISSA EDDY, Associated Press Writer, 27 Feb 2008
…secret services’ ability to use virus-like software to monitor suspected terrorists’ online activity.The court rightly said suspicion is not enough:
“Given the gravity of the intrusion, the secret infiltration of an IT system in such a way that use of the system and its data can be searched can only be constitutionally allowed if clear evidence of a concrete threat to a prominent object of legal protection exists,” Papier said.And a judge has to approve it.
Now that’s risk management.
-jsq
Most of the whining comes because Office 2008 does not include Visual Basic. In some respects, this is welcome change because Office never should have had Visual Basic. VBA is what enabled the Macro Virus. Furthermore, Office 2009 (for Windows) is not going to have VBA, either.The poster immediately goes on to sneer at OpenOffice for allegedly not being able to do things Office can do (without ever mentioning specifics) and at Keynote because everybody uses PowerPoint (while acknowledging that “Keynote rocks — it got Al Gore both an Oscar and the Nobel Prize”).However, not shipping VBA in Office 2008 means that people who want to have cross-platorm documents that are pseudo-applications have to deal with it in 2008, not 2009. That’s worth complaining about.
— Microsoft Has Trouble Programming the Intel Architecture, by mordaxus, Emergent Chaos, 16 Jan 2008
When Microsoft can manage to annoy even slavish users like that by breaking backwards compatibility, MSFT has a problem. No doubt no VBA in Office isn’t the last straw, but it isn’t the first, either.
-jsq
The UK government has published guidelines for the application of a law that makes it illegal to create or distribute so-called “hacking tools”.How long will it be before a simple traceroute gets you not only disconnected from your ISP but also clapped in jail for “hacking”?…
A revamp of the UK’s outdated computer crime laws is long overdue. However, provisions to ban the development, ownership and distribution of so-called “hacker tools” draw sharp criticism from industry. Critics point out that many of these tools are used by system administrators and security consultants quite legitimately to probe for vulnerabilities in corporate systems.
The distinctions between, for example, a password cracker and a password recovery tool, or a utility designed to run denial of service attacks and one designed to stress-test a network, are subtle. The problem is that anything from nmap through wireshark to perl can be used for both legitimate and illicit purposes, in much the same way that a hammer can be used for putting up shelving or breaking into a car.
— UK gov sets rules for hacker tool ban, Consultants in frame? Definitely Maybe By John Leyden, The Guardian, Published Wednesday 2nd January 2008 15:54 GMT
It gets better: Continue reading