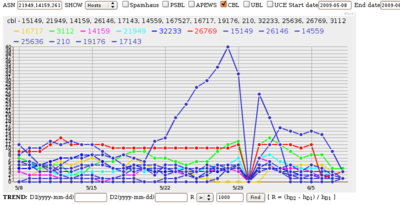
It turns out the source of the big spam surge that rocketed eight ASNs
| Rank (Previous) | ASN | |
|---|---|---|
| 1 | (9) | AS 21788 NOC |
| 2 | (-) | AS 27229 WEBHOST-ASN1 |
| 3 | (-) | AS 46475 LIMESTONENETWORKS |
| 4 | (-) | AS 33055 BCC-65-182-96-0-PHX |
| 6 | (5) | AS 15149 EZZI-101-BGP |
| 7 | (-) | AS 13768 PEER1 |
| 8 | (-) | AS 10439 CARINET |
| 9 | (-) | AS 7796 ATMLINK |
So, Ogee is not a botnet; it is a collection of IP addresses apparently involved in snowshoe spam. It’s also not new. Ogee is just a specific set of snowshoe addresses. But what is snowshoe spam?
Paul Roberts wrote for ThreatPost 6 October 2011, Expert: Eight Years Later, ‘Snowshoe Spam’ Suggests CAN SPAM Not Working,
Brett Cove, a researcher for anti malware firm Sophos, told attendees at the annual Virus Bulletin Conference on Thursday that so-called “snowshoe spam” is becoming a bigger problem, even as spam e-mail volumes associated with botnets are receding. Snowshoe spam is responsible for the bulk of spam messages that make it past anti spam filters at U.S. firms, even as bulk senders avoid prosecution by adhering to the letter of the U.S. CAN SPAM anti-spamming law.Snowshoe spam isn’t a new problem. In fact, within anti spam circles, researchers have been talking about the phenomenon for years. The term “snowshoe” spam comes from the tactic of spreading the load of spam runs across a wide range of IP addresses as a way to avoid detection by anti spam filters, in the same way that snowshoes spread the weight of their wearer across a wide area to avoid breaking through snow and ice.
Anti spam filters are typically programmed to allow only a small volume of identical e-mail messages from the same IP address range, Cove told Threatpost. Snowshoe spam is able to avoid—or postpone—the filters by sending mail from a range of addresses, often leased by the bulk mail senders, he said.
That may sound a lot like low-and-slow botnet spamming, but there are five key differences:
Continue reading