“If Windows CE is taken up in a big way in a large market we may see some increased malware activity,” he warned.Continue reading“There is not a lot of functionality built in that will stop attacks on that platform, so there could be a problem if it takes off. As for other operating systems there has been very little new activity.”
Windows use could boost mobile malware Increasing use of Windows CE could leave mobile users vulnerable, Iain Thomson, vnunet.com 15 Nov 2006
APWG eCrime @NCSF
Fatter Phishers
-jsq
Security Clerks
Most C-level executives view security as an operational issue — kind of like facilities management — and not as a strategic review. As such, they don’t have direct responsibility for securityWhy should executives get involved with directly managing a bunch of clerks over a bunch of stuff? Continue readingWhy Management Doesn’t Get IT Security, Bruce Schneier, 8 Nov 2006
Such attitudes about security have caused many organizations to distance their security teams from other parts of the business as well. “Security directors appear to be politically isolated within their companies,” Cavanagh says. Security pros often do not talk to business managers or other departments, he notes, so they don’t have many allies in getting their message across to upper management.Kicking Some Brass, Tim Wilson, DarkReading, NOVEMBER 2, 2006
Politics and Net Neutrality
To some extent, I had given up on America and the prospect that it would develop a regulatory framework that might enable Internet entrepreneurs. In my mind, other countries have been supplanting the US as the havens for Internet innovation. The midterm election, however, has reminded me that, in a democracy, there is always room for a rethink, a do-over, an opportunity for a dramatic policy shift when the national consciousness wakes up and recognizes that its policies might be leading the nation down a backward-heading path.What could this shift be? Continue readingShift Happened: How Might a Democrat-Controlled Congress Affect Media, Internet, Communications and Entertainment? Jeff Pulver, Jeff Pulver Blog, November 09, 2006
Congressional Confusopoly
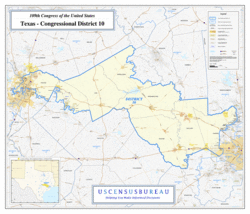 Have you noticed how difficult it is to find accurate maps of
U.S. Congressional districts?
The ones the
New York Times is using in its election coverage are out of date,
and the Times is far from alone in this error.
A correct map is on the right; more on that below.
Have you noticed how difficult it is to find accurate maps of
U.S. Congressional districts?
The ones the
New York Times is using in its election coverage are out of date,
and the Times is far from alone in this error.
A correct map is on the right; more on that below.
European Power and Network Outage
 The European power outage of last Saturday 4 November that left
about 10 million people wthout power
also had quite a few effects on
Internet connectivity in Europe, such as those shown in the animation.
Apparently backup power sources don’t solve everything.
The European power outage of last Saturday 4 November that left
about 10 million people wthout power
also had quite a few effects on
Internet connectivity in Europe, such as those shown in the animation.
Apparently backup power sources don’t solve everything.
-jsq
FBI Fishes Phishers
A large group of suspected internet fraudsters has been arrested following an investigation by the FBI.Good on the FBI! Continue readingSeventeen individuals have been arrested, four in the US and the rest in Poland, after being chased by over 20 different FBI offices.
The group is accused of carrying out a phishing attack against a major financial institution in the three months from August 2004, it is claimed.
Police arrest suspected phishing gang Richard Thurston, ZDNet UK, 03 Nov 2006
Net Neutrality Podcast
 Here’s
a picture and a podcast from the
EFF-Austin net neutrality forum of the other day.
Lots of interesting back-and-forth in there, among the panelists
and the audience.
Here’s
a picture and a podcast from the
EFF-Austin net neutrality forum of the other day.
Lots of interesting back-and-forth in there, among the panelists
and the audience.
Jonl quotes my blurb about the FCC’s principles emphasizing consumers, i.e., consumers of broadcast media, while Internet growth is fueled by groups of participants; I previously posted a bit more about that.
-jsq
PS: Yes, despite how it looks in the picture, I am wearing a shirt.
Ipsos Custodies
However, an easy way occured to me how somebody could subvert these local machines; a way that doesn’t even involve modifying the software, wireless networks, or any access to the machine other than through the voting interface. Continue reading