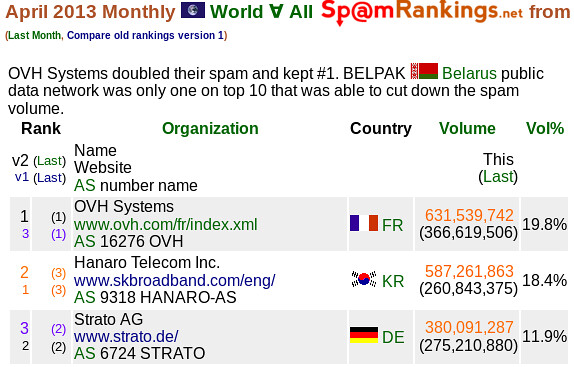
 OVH Systems’ AS 16276 is #1 in
the April 2013
OVH Systems’ AS 16276 is #1 in
the April 2013
 worldwide from CBL data
with
631,539,742 spam message seen according to
the new Version 2 of SpamRankings.net,
while
the same ASN is #3 in
the old version 1 rankings with 363,884,989 spam messages seen.
Why the difference?
worldwide from CBL data
with
631,539,742 spam message seen according to
the new Version 2 of SpamRankings.net,
while
the same ASN is #3 in
the old version 1 rankings with 363,884,989 spam messages seen.
Why the difference?
The difference is because Version 2 finds more netblocks assigned to AS 16276. Specifically:

| 72 | netblocks currently assigned |
| 27 | netblocks previously assigned |
| 14 | netblocks are persistant |
| 58 | netblocks have been added |
| 13 | netblocks have been removed |
Many more netblocks were found for AS 16276 only by Version 2 than were found only by Version. So the difference in the amount of spam presumably comes from those added netblocks. Yes, we can drill down and see, and we may do that later.
-jsq
 Turkey from CBL data
Turkey from CBL data






 for
for
 Canada.
Canada.