Commenting on the previous post, Adam wants to know:
“But…but…what is a cat bond? How does it work? When does it pay? Does it have coupons? Who gets what risk with them?”
Fair enough.
Cat bond is short for catastrophe bond. A cat bond is somewhat like a municipal bond, except if the catastrophe occurs, the principal goes away to deal with the catastrophe.
Why would anyone buy a bond that could vanish? The principal of almost any investment could disappear, as many of us who invested in stocks in the late 1990s can attest. Even a municipal bond can be downgraded and thus lose value. And while the precise time of occurence of a catastrophe such as an earthquake, hurricane, flood, or wildfire may not be predictable, the probability of its occurence during, e.g., a ten year period is usually fairly well known, and not as susceptible to politics or market fads as some other investments. At the least, the risk of loss of principal of a catastrophe bond is not strongly correlated with risk of loss of principal of other investments.
And catastrophe bonds typically pay a higher percentage than other bonds.
Who buys them? Usually not individuals, rather lreinsurers, insurers, commercial banks, hedge funds, and investment advisors.
Who issues them? Financial houses, insurance companies, and hedge funds.
Why? To increase the pool of available capital to cover large risks.
For example? Packages of credit card debts, mortgages, or automobile loans. Force majeure events such as earthquakes, floods, and hurricanes.
The application of cat bonds to Internet force majeure events seems straightforward. Except, of course, that probability matrices are needed to write them.
Is that what you wanted to know, Adam?
-jsq
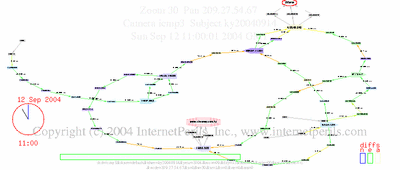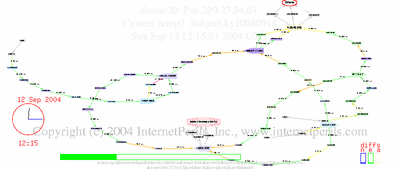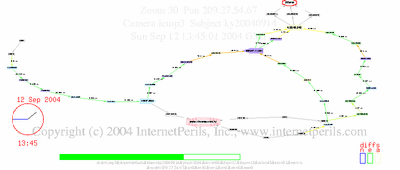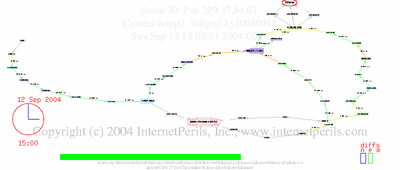
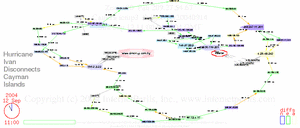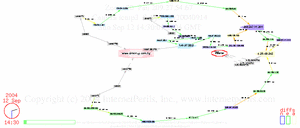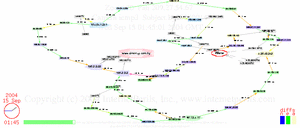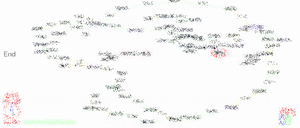 Here’s an update showing the whole period of disconnect, two days off the net, and reconnect, with details about undersea cables and comparison to Jamaica.
Here’s an update showing the whole period of disconnect, two days off the net, and reconnect, with details about undersea cables and comparison to Jamaica.
 I
I
