 Well, this should seem obvious:
Well, this should seem obvious:
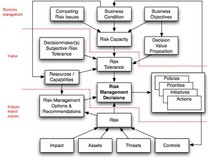
For quite a while now, I’ve been claiming that in order for InfoSec to do it’s job properly, it needs to understand the business.
— Whose Line Is It Anyway? Arthur, Emergent Chaos, 10 July 2007
Let’s go a bit farther:
Yesterday, Jack Jones again showed that he’s in the same camp when he asked us: "Risk Decision Making: Whose call is it?" There he shares his thoughts how to decide whether or not the Information Security team should be making information risk decisions for a company or if that should come from upper management.
I would claim that this shouldn’t be an either/or question: it’s a both/and.
Continue reading

 It’s that time again:
It’s that time again: